Security Upskill Programma
Ons Security Upskill Programma helpt je om rolgebaseerde en progressieve learning journeys op te stellen op basis van de benodigde Security skills binnen jouw team. Deze skills kunnen modulair worden geleerd voor elke positie binnen het team, ongeacht de mate van ervaring en kennis.
Training op maat voor jouw organisatie?
Michiel helpt je graag verder met op maat gemaakte trainingsoplossingen voor jouw teams of onderneming.
Rolgebaseerde en progressieve learning journeys
01
Het Security Upskill Programma biedt je rolgebaseerde en progressieve learning journeys die geschikt zijn voor alle personen die betrokken zijn bij het ontwikkelingsproces. Een uniforme securitytraining werkt niet. Daarom kan je gespecialiseerde kennis en skills opdoen die op maat gemaakt zijn voor de verschillende rollen binnen het Security ontwikkelingsproces.
Modulaire en uitgebreide aanpak voor het gehele team
02
Het programma is onderverdeeld in modules die verschillende aspecten van Security behandelen, van basisconcepten tot cloud security en DevSecOps. Elke module behandelt diverse onderwerpen, waardoor het programma eenvoudig kan worden aangepast aan de specifieke behoeften van uw beveiligingsteam.
Focus op specialisatie en schaalbaarheid
03
Traditionele beveiligingstrainingen leggen vaak de nadruk op specialisatie of schaalbaarheid. Dit programma probeert die kloof te overbruggen door gespecialiseerde training aan te bieden voor verschillende rollen en tegelijkertijd schaalbaarheid te garanderen door gemeenschappelijke basiskennis aan te bieden en samenwerking tussen teamleden en belanghebbenden te bevorderen.
Waarom zou je
jouw team(s) trainen?
Met nieuwe technologieën die zich razendsnel ontwikkelen en een uitdagende banenmarkt is het vinden en behouden van de juiste mensen een lastige taak.
Maar, er is eerder een tekort aan de juiste vaardigheden dan aan mensen. Daarom zal 50% van alle werknemers zich de komende vijf jaar moeten bijscholen, waarschuwde World Economic Forum ons.
Jouw werknemers trainen is dan ook de beste oplossing om die skills gap te overbruggen. Nieuwe skills leren, geeft werknemers de voldoening dat ze investeren in zichzelf en hun toekomst. Bovendien vergroot dat hun betrokkenheid bij jouw organisatie, omdat ze weten dat hun werkgever in hen investeert. Ze voelen dat ze er toe doen.
Op dezelfde manier trekken talenten sneller naar organisaties waar zij zich persoonlijk kunnen ontwikkelen. Bovendien is het opleiden van jouw mensen tussen de 72% en 90% goedkoper dan het zoeken naar en het aannemen van nieuw talent.
Voordelen van het bijscholen van uw organisatie
Verbeter jouw financiële resultaten met verbeterde vaardigheden.
Vergroot de betrokkenheid en tevredenheid van werknemers.
Behoud werknemers langer voor jouw organisatie.
Verhoog de efficiëntie en productiviteit van het team.
Trek nieuw talent aan door aantrekkelijke doorgroeimogelijkheden.
Bereid je beter voor op toekomstige veranderingen.
Hoe kun je jouw Security team het beste trainen?
Heb jij die indruk ook niet? Dat veel Security trainingsprogramma’s zich te vaak focussen op de mening van één expert of het simpelweg uitzenden van algemene Securityprincipes over een hele organisatie?
Het probleem met deze benaderingen is dat je ofwel specialisatie OF schaalbaarheid hebt, maar nooit beide. Om wel die specialisatie op schaal te krijgen en de juiste informatie met de juiste mensen te delen, heb je een andere aanpak nodig.
Met ons zelfontwikkelde Security Upskill Programma en de onderliggende learning journeys zullen jij en jouw team(s) met rolgebaseerde en progressieve learning journeys de juiste kennis opdoen. Alle mensen die betrokken zijn bij jouw Security ontwikkelproces krijgen zo de training die alleen zij nodig hebben, met de verdieping die ze nodig hebben.
Om je team(s) en teamleden nieuwe skills te leren, hebben we een Security Upskill Programma ontwikkeld dat elke functie en elke verantwoordelijkheid omvat.
Om een veilige cultuur en ecosysteem te creëren, moeten de leden het grotere geheel en elkaars verantwoordelijkheden begrijpen.
Deze module helpt je met een algemeen begrip van beveiliging en het bijbehorende jargon. Door dit te begrijpen verdwijnen dubbelzinnigheden, aannames en vage of onduidelijke (beveiligings)eisen. We creëren ook een gemeenschappelijke basis tussen alle teamleden en belanghebbenden.
Met een vooraf gedefinieerde en gestandaardiseerde aanpak kun je voorspelbare activiteiten inbedden in plaats van je bezig te houden met werk dat buiten de scope valt. Het zorgt ook voor feedbacklussen om herhaling van fouten te voorkomen.
Deze module verduidelijkt jouw uitdagingen en oplossingen bij het implementeren van secuirty in een development lifecycle. Leer waar je op moet letten in elke ontwikkelingsfase en hoe elk teamlid de meest effectieve security kan waarborgen.
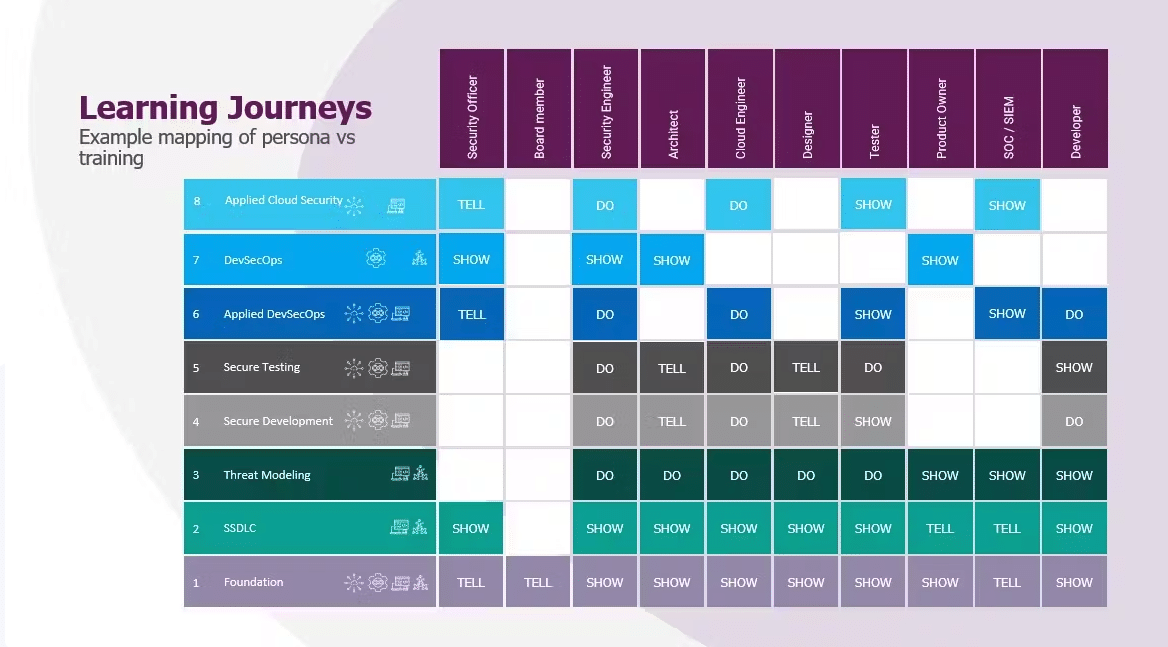
Voorbeeld van jouw Security Learning Journey
Als je de bovengenoemde aandachtsgebieden en smaken neemt en deze elementen combineert in een modulaire learning journey, kom je tot het overzicht hiernaast. Elke rol kan zijn eigen weg volgen, zich aanpassend aan jouw behoefte en complementair aan de al aanwezige skills.
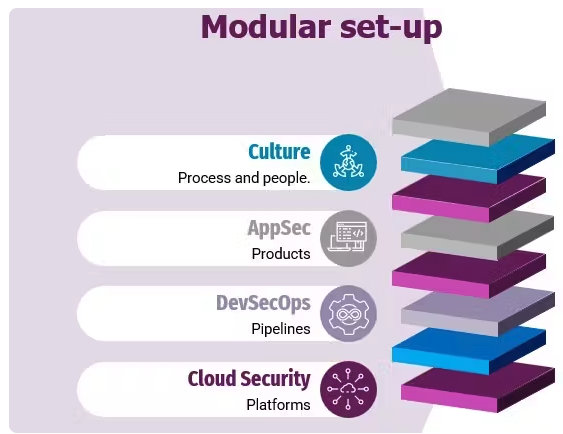
Modulaire opzet
Om jouw upskillprogramma af te stemmen op de behoeften van je team, hebben we gekozen voor een modulaire opzet met verschillende ‘smaken’ en focusgebieden.
Aandachtsgebieden voor Security training
Laten we eerst de verschillende aandachtsgebieden bespreken. Zoals je in de onderstaande afbeelding kunt zien, hebben we pictogrammen gebruikt om de aandachtsgebieden van een module weer te geven. Een module van het leertraject beveiliging kan meer dan één van deze gebieden vertegenwoordigen:
- Proces en mensen
- Producten
- Pijpleidingen
- Platformen
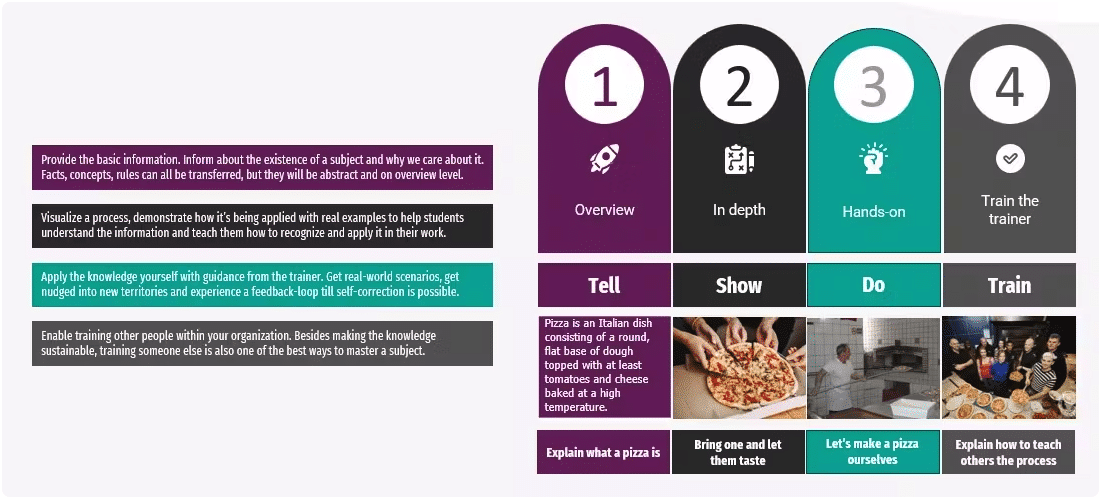
De Security ‘smaken’
Naast de verschillende focusgebieden geven we een module ook een bepaalde ‘smaak’. Wat betekent dat, een smaak?
Een smaak geeft aan hoe ver je bent gekomen in je kennisreis. We hebben dat gebaseerd op vier ervaringsniveaus:
- Vertellen: basisinformatie krijgen over een bepaald onderwerp.
- Laten zien: laten zien hoe het wordt toegepast met voorbeelden uit de praktijk.
- Doen: de kennis zelf toepassen met scenario’s uit de praktijk.
- Train: geef les aan anderen in jouw organisatie om kennis te verspreiden en het onderwerp onder de knie te krijgen.
Samenwerkingsverbanden


Trainingsformats
We bieden trainingen aan in elke gewenste format en bij elke gewenste partner. Of je nu de voorkeur geeft aan klassikaal leren, virtuele, klassikale training, blended learning, of e-learning, samen creëren we het beste trainingsprogramma op maat.

Klassikale Training
De klassikale training is gebaseerd op een mix van dynamische lessen en praktische opdrachten. We maken leren leuk door het gebruik van spellen en andere interactieve leermethodes.

Online Training
In de online, klassikale trainingen gebruiken onze trainers verschillende tools en scènes om een optimale ervaring te bieden, zodat je ook op afstand interactie tussen de deelnemers hebt.

On-Demand Training
Xebia Academy is een officiële reseller van on-demand trainingen van toonaangevende platforms, zoals Acloudguru, Pluralsight en Qwiklabs. Met korting krijg je toegang tot deze platforms.
Maak kennis met de trainers

Marinus Kuivenhoven
Marinus Kuivenhoven is a Security trainer and Head of Security Learning and Coaching at Xebia Academy.

Dave van Stein
Meet Dave van Stein, trainer at Xebia Academy. Dave is a security trainer and trains on behalf of Xebia the Risk Assessing User Stories and Secure Coding Fundamentals courses. View Dave’s full profile and training courses on Xebia Academy.

Vraag me alles!
Neem contact op met Michiel Zeinstra, onze Training Advisor. Hij helpt je graag met al je vragen!
