I recently had a conversation with a customer who is working with Azure DevOps and wants to implement SonarCloud. My colleague had an article about that 4 years ago, but tools continue to evolve so here’s an update on that.
SonarCloud did an amazing job on guiding you through setup on their side (see the docs). However, there is a gap in what you need to do on the Azure DevOps side. My goal is to fill this gap.

I asume that you already have set up an organization and your project in SonarCloud. If not, do so and keep the required Azure DevOps PAT (Personal Access Token) with the Code (read and write) permissions for later usage. Fine, now we will enable each tool to interact with the other.
Enable SonarCloud for Pull Request Analysis with Azure DevOps
First enable SonarCloud for interaction with Azure DevOps. This can be set up in the Administration Tab.
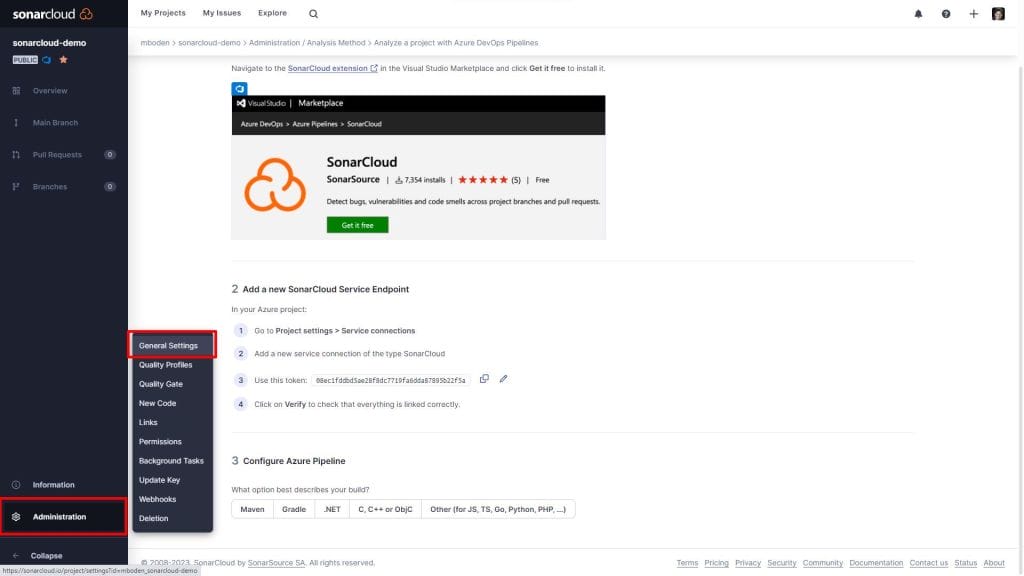
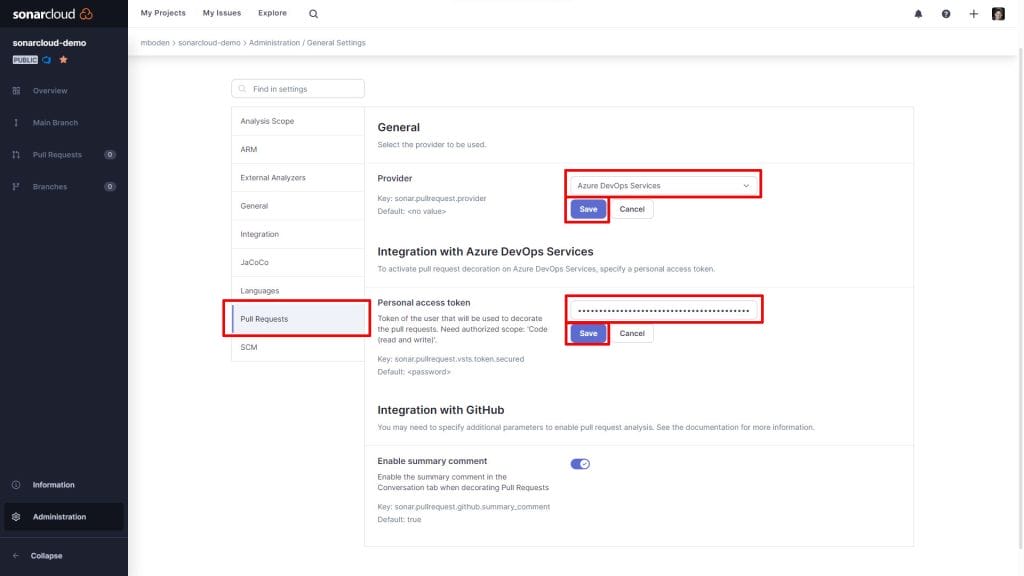
In the Pull Request Menu select the Provider Azure DevOps Service and enter an Azure DevOps Personal Access token with Code (read and write) permissions (I used the same as for importing the organization).
Do not forget to click on both save buttons!!!
Trigger SonarCloud Analysis from Azure DevOps Pipelines
Afterwards set up Azure DevOps to interact with SonarCloud. Go back to the project start page and choose With Azure DevOps Pipeline as your analysis method.
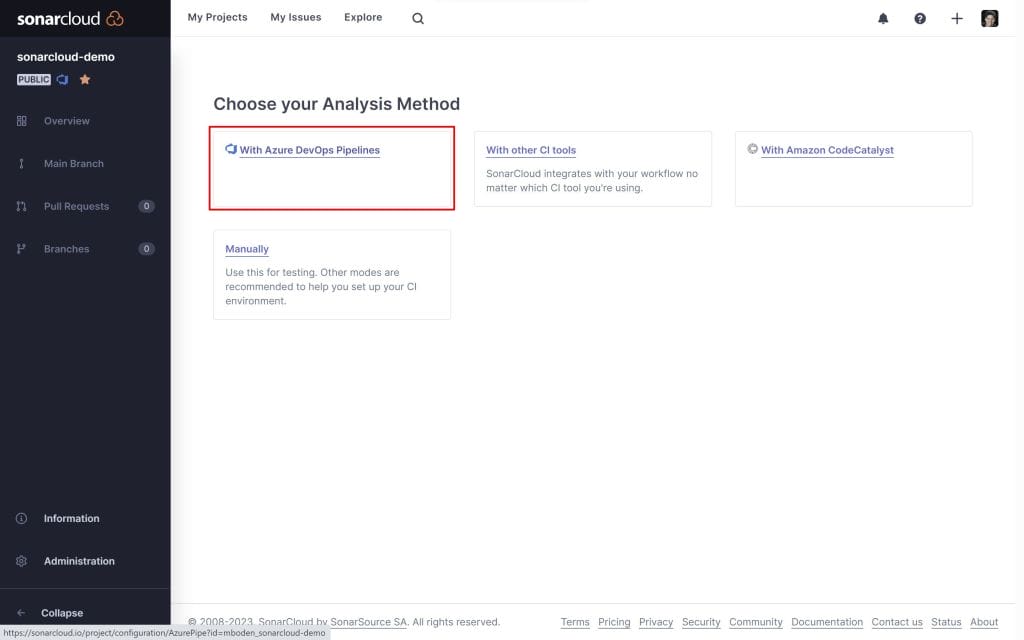
This guides you through installing the necessary extension in your AzureDevOps organization and gives you a token, that you can use to create a service connection to SonarCloud in your Azure DevOps project.
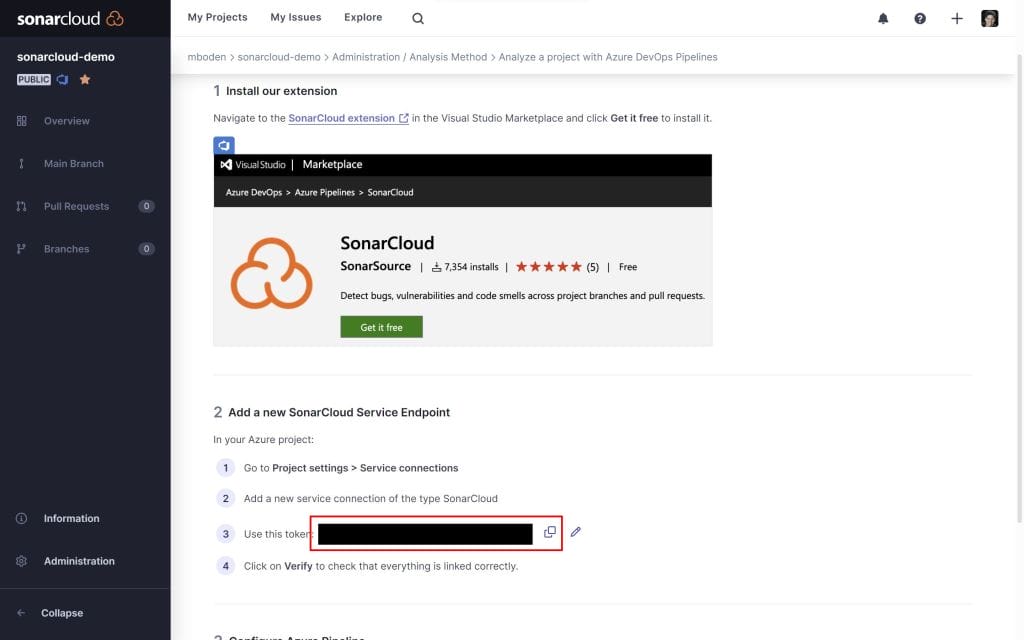
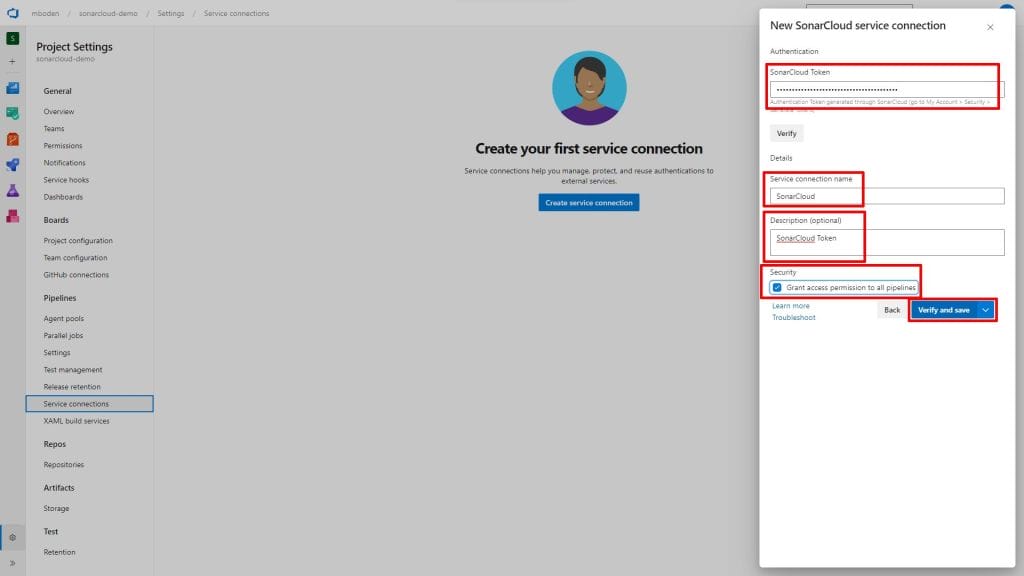
As I want to analyze a JavaScript project, I’ll choose the option other Other to configure my pipeline. This gives me detailed instructions on how to configure the SonarCloudPrepare task.
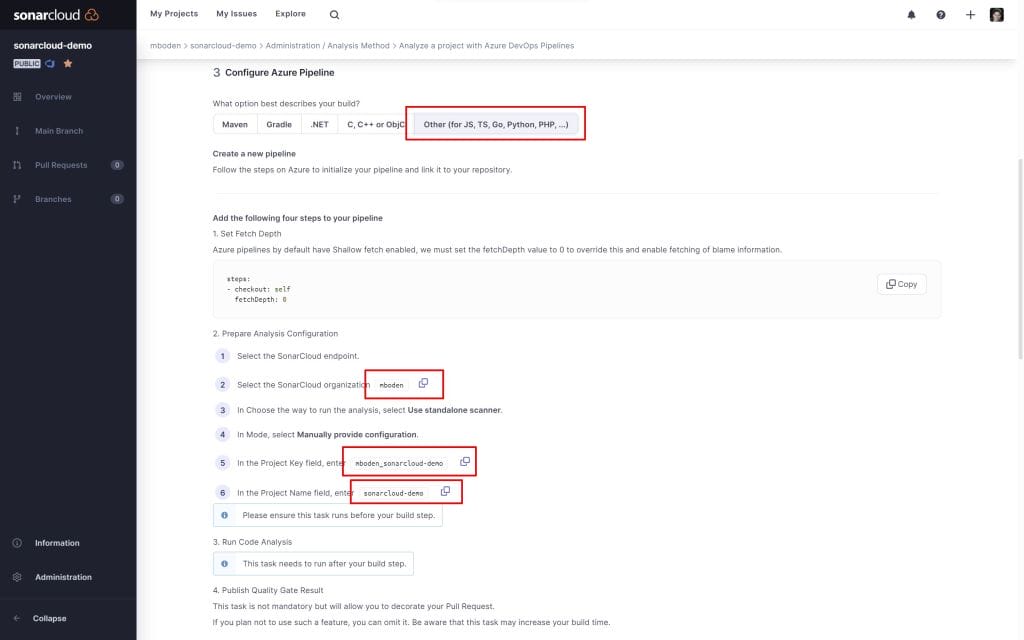
The pipeline for my JS project looks like this:
# Node.js
# Build a general Node.js project with npm.
# Add steps that analyze code, save build artifacts, deploy, and more:
# https://docs.microsoft.com/azure/devops/pipelines/languages/javascript
trigger:
branches:
include:
- 'main'
pool:
vmImage: ubuntu-latest
steps:
- checkout: self
fetchDepth: 0
- task: NodeTool@0
inputs:
versionSpec: '16.x'
displayName: 'Install Node.js'
- task: SonarCloudPrepare@1
inputs:
SonarCloud: 'SonarCloud' # name of your SonarCloud service connection
organization: 'mboden' # name of the SonarCloud organization as given above
scannerMode: 'CLI'
projectKey: 'mboden_sonarcloud-demo' # SonarCloud project key as given above
projectName: 'sonarcloud-demo' # SonarCloud project name as given above
displayName: 'SonarCloud Configure'
- script: |
npm install
displayName: 'Install Dependencies'
- script: |
npm run tslint
displayName: 'Lint'
- script: |
npm run build
displayName: 'Build'
- script: |
npm run test
displayName: 'Test'
- task: SonarCloudAnalyze@1
inputs:
jdkversion: 'JAVA_HOME_11_X64'
displayName: 'SonarCloud Analyze'
- task: SonarCloudPublish@1
inputs:
pollingTimeoutSec: '300'
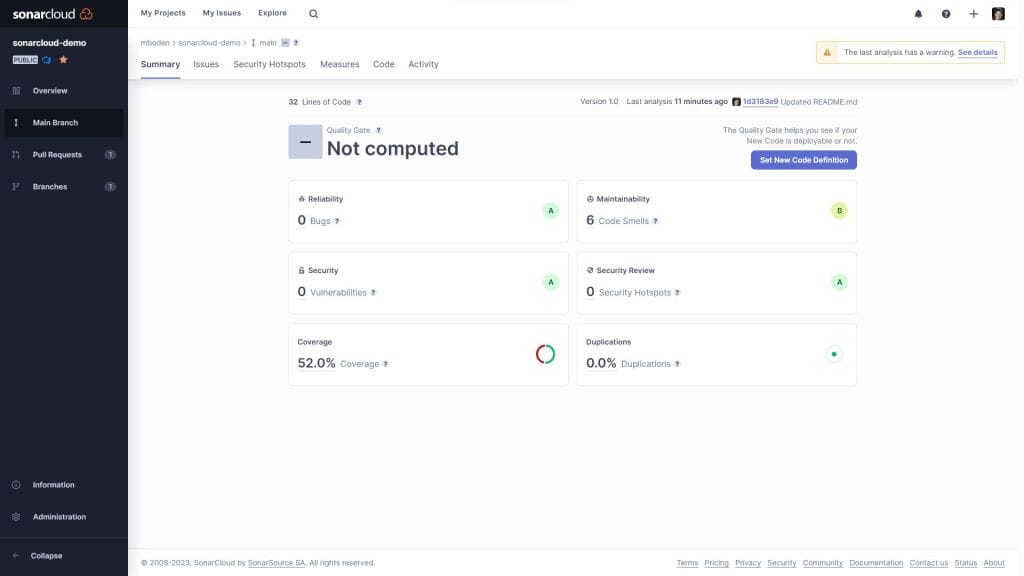
displayName: 'SonarCloud Publish'Setting up this pipeline in Azure DevOps and running it once will already show some results for the main branch in SonarCloud.
Now I want to analyze a topic branch and make use of the pull request quality gates of SonarCloud. This requires me to set up some branch policies for the main branch.
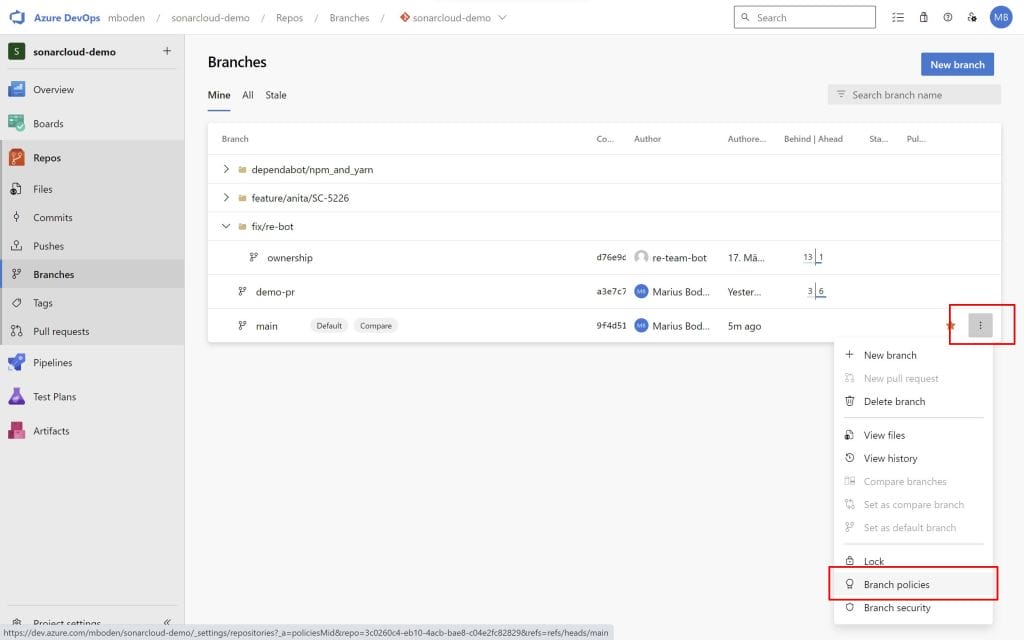
Enabling Check for comment resolution will require any reviewer of the pull request to resolve the comments made by SonarCloud within the pull request. To enable pull request validation in SonarCloud a build validation for the pipeline has to be set up.
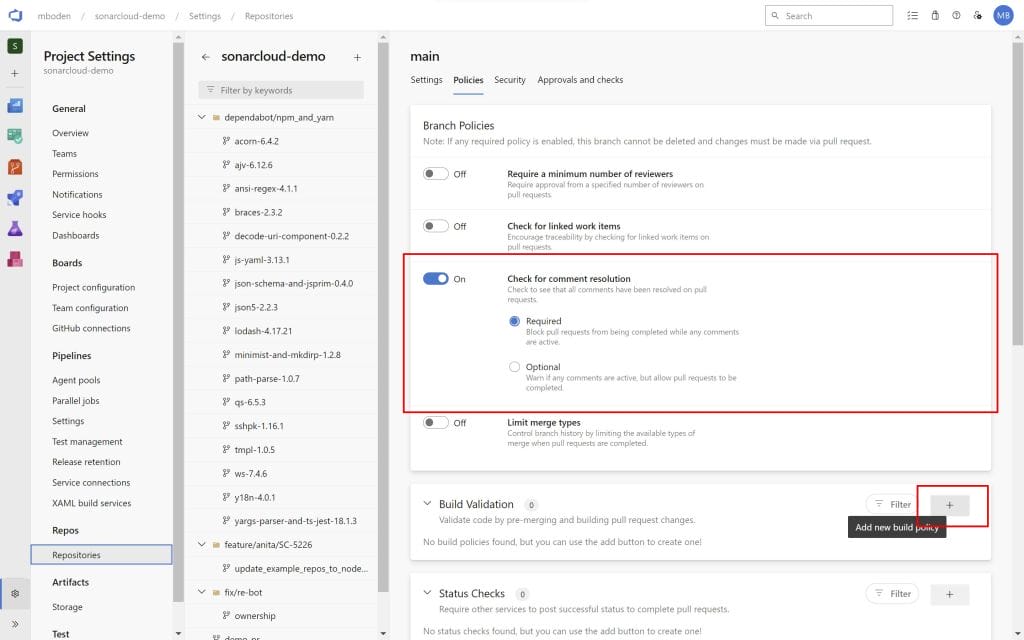
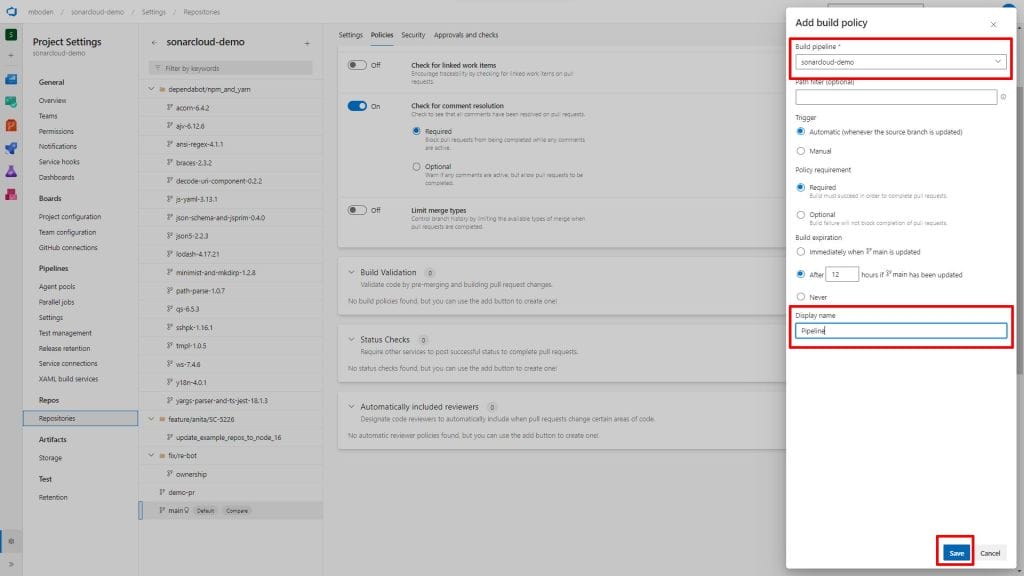
I select the sonarcloud-demo pipeline I created earlier, leave all settings to default and give it a nice display name.
Now everything is set up to create a branch, check in some code that does not pass the validation and push it to the repo. Afterwards I will create a pull request to see the quality gates failed. As we can see, SonarCloud did all the checks and not only we can see the quality gates are not passed but sonarcloud also created comments with necessary changes.
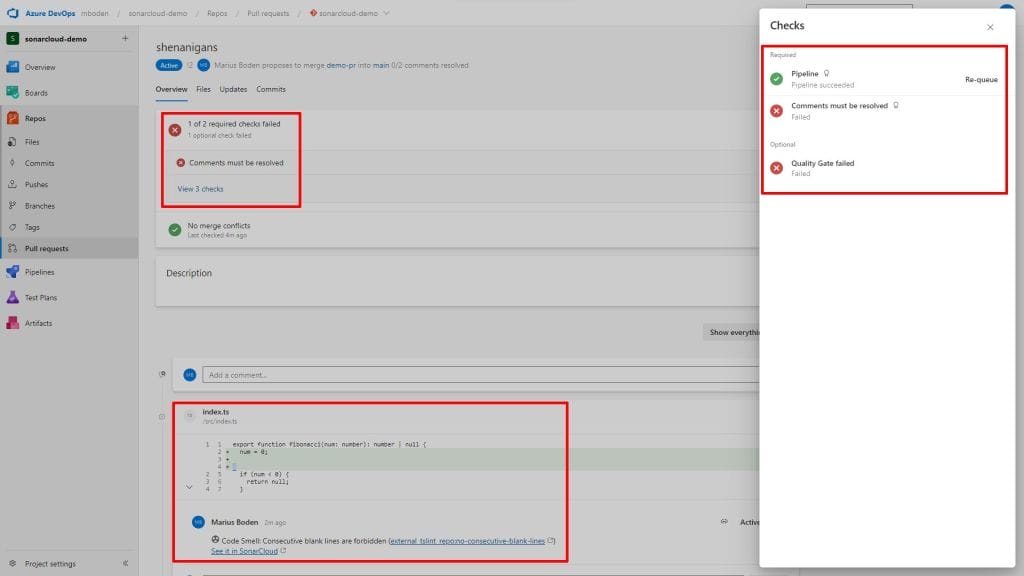
A click on Quality Gate Failed directly redirects to SonarCloud.
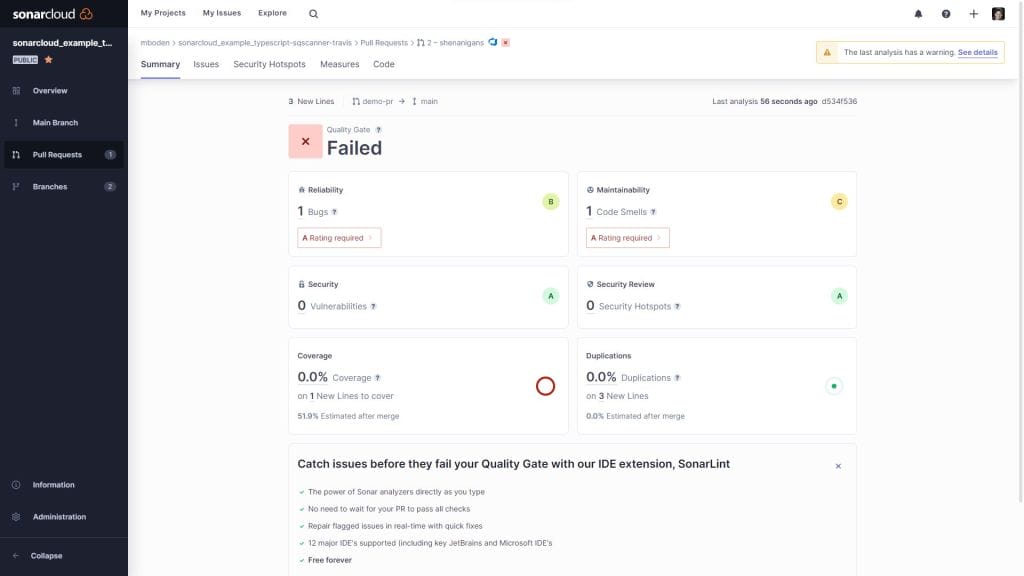
After running this once on a pull request, azure devops got the first analysis results and you can setup status checks. This will prevent the pull request from being merged as long as the quality gates are failed. To do so switch again to the the branch policy settings for your default branch.
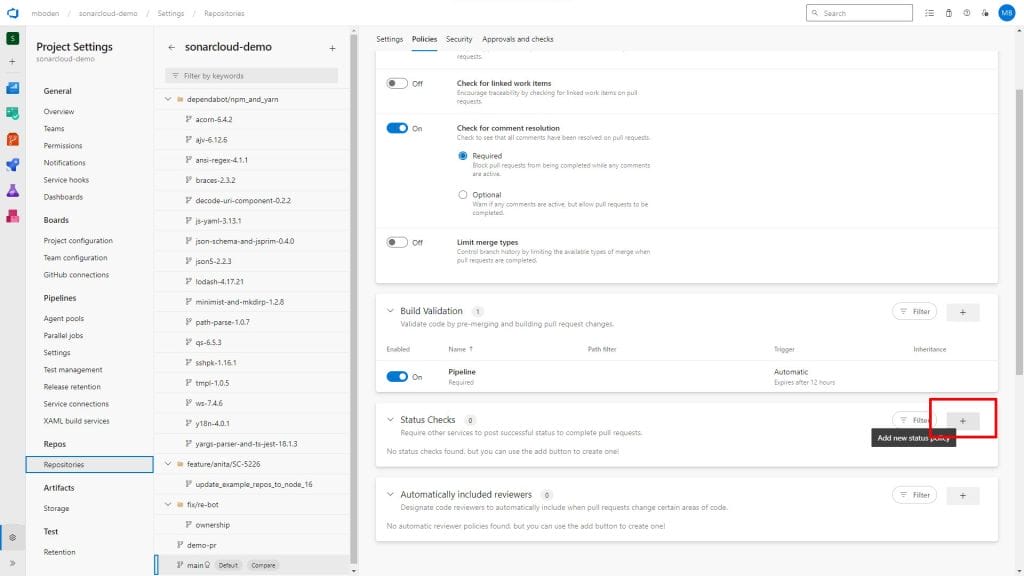
Select the status check and either give custom Genre and Name or stay with the defaults. Click save.
Note: The pipeline has to run at least once for a pull request, before the corresponding status checks will appear in the Dropdown list.
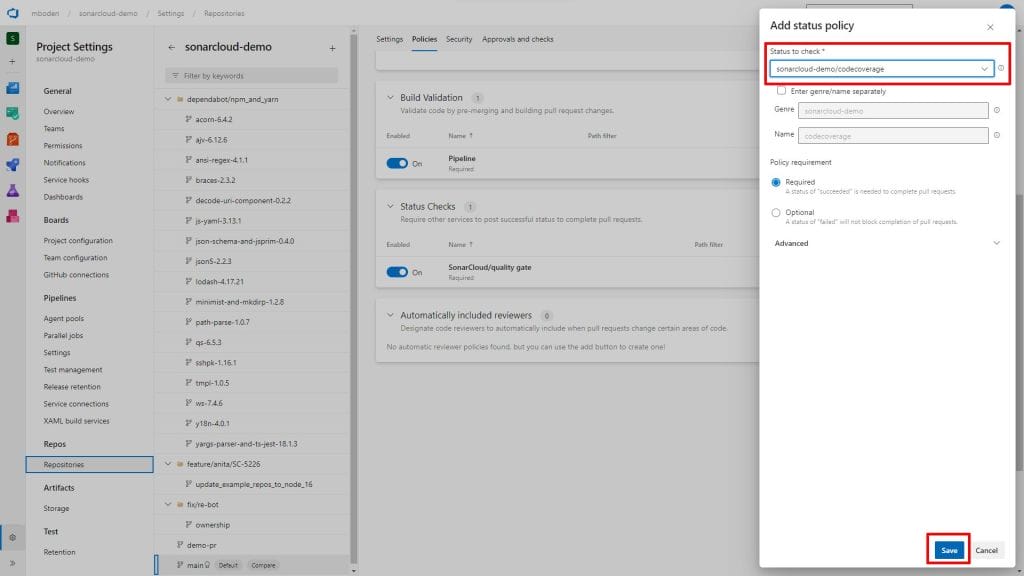
That’s it! We successfully integrated SonarCloud code quality checks with Azure DevOps pipelines and pull requests and prevent pull request from being merged before the quality gates are passed and detected issues are resolved.
Links
Sonarcloud Project: Sonarcloud AzurePipe Project
Azure DevOps Project: Azure DevOps Sonarcloud Demo Project
Azure DevOps Pull Request: Azure DevOps Pull Request 2




