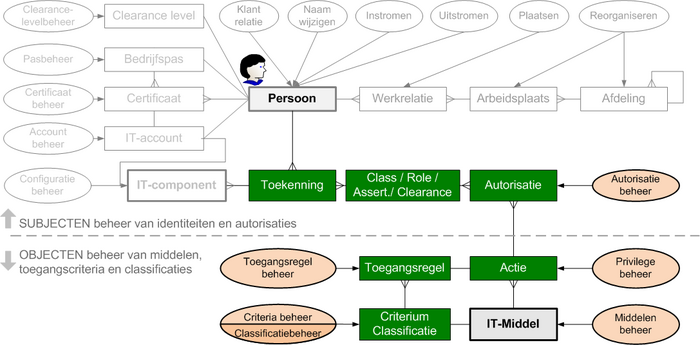
We all know that the hardening of a system or implementing 2FA does not magically improves the security of an organisation. For a successful implementation of IAM, PKI a holistic approach is needed. Also for the successful improvement of security in your organisation, a holistic approach is needed. Implementing and improving security demands your approach to cover both people, process and technology.
This blog provides you with a mental model on how to change behavior of people and how to change the culture of an organisation. To change the culture of your organisation you need to change the structures and lead by example. And there is more to it, why this works in changing the behavior of individual persons.
I also highlight material to facilitate a workshop that helps you in making the mental models behind the behavior of people explicit.
Security is never one object or one control.
Below a few examples on PKI (Public Key Infrastructure), IAM (Identity and Access Management) and the ISO2700-series of Information Security Standards, to visualize the holistic approach in these topics. Security is so much more than a software engineering topic.


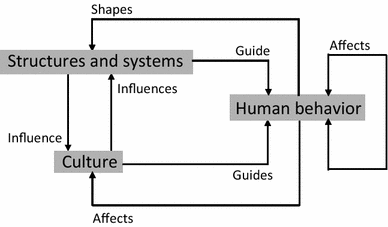
Improving Security implies changing human behavior
Holistic in the context of security implies that security is never about engineering only, it is about the collaborative implementation of the famous trinity of People, Process and Technology (PPT) [1], [2], [3], [4].
I am fascinated by the People part since this is a domain that is most alien to me.In IT the concept of culture plays a role in the famous CALMS of DevOps [5], and in Modern Agile [6], [7], [8] the role of personal safety plays an important role for a team to perform.
At Xebia Security we define security as a capability of the organisation. This capability comes to light as:
- Quality Attribute in ISO 25010,
- Security and Privacy by design in the GDPR and as
- Business Continuity and Information Security in Risk Management (ISO 31000) [9], [10].
To improve security you need to change the behavior of the people in the organisation.
Behavior of an employee
Behavior in the context of an organisation is influenced by the Process (Structure and Systems) and the Culture (Hoogervorst 2018) [11]. This circular relation is called the Morphogenetic Social System Model [by Margaret Archer], [12], [13], [14].
Behavior of management
There are two types of behavior at the center of the model in Hoogervorst 2018.

When I started my research on human behavior I thought these models of Hoogervorst where out-of-scope, since I am interested in what makes one person behave and not searching for the role of Management and going towards Organisation Behavior Management (OBM). But… I was wrong on Hoogervorst.
Behavior, mental models and interpretation
When I did some research on the topic of human behavior, it appears that mental models play a large role.
The literature states that we as a human observe the world, and use our personal mental models to interpreted the events we see and then determine for our-self what action to take. Here are a few variations on this concept. You will recognize that most models use a circular relationship in the observations, interpretations and actions.
I was wondering if there is something on the topic of the interpretation of the models, since when our clients together with us want to to improve the level of security at their company, experience shows that providing (yet) another model to the employees does not guarantee improvement, no matter how good we try.
Providing new models and new information only adds to the noise of the already complex work environment. This is not the way to make lasting impact in an organisation.
What drives behavior of a person?
Fred Korthagen created in 2001 the onion model [16], which is a popular (mental) model in the Dutch education system. The onion model is applied in learning how to improve the capability of a person by applying the method of reflection [17].
Reflection is the process of looking back at behavior and then taking actions to change the behavior in the future.
The onion model is similar to the Dilts Pyramid [18]. This is a model created by Robert Dilts in 1990, 1996 representing the various Neuro-Logical Levels in a person [19]. The Dilts Pyramid is often used in the context of behavioral change management.
Note: Both models are inspired by earlier work of Bertrand Russell and Gregory Bateson, who are know for their work on meta-communication and type-theorie. Which is in-itself another rabbit hole to dive into.
In the figure below I visualized the Onion and the Pyramid. The outside layers are the first to interact with the outside reality and the further you peal the onion, you come to the personal reality and personality of a person.
The onion of Korthagen and the pyramid of Dilts state that behavior of a person is the result or dependend on the four underlying layers.
To change the behavior of a person you need to influence the “Skills and Capabilities”, and to trigger the adaption of the skills it is important to trigger the “Values and Believe” system, which is founded upon the “Identity” of a person.
Small deviation from the story line
See here why Modern Agile states that personal safety is important to have an high performance team, since the adaption of new skills and capabilities in a high pace is highly demanding on your values and believe system.
See also here the link to SRE (Site Reliability Engineering). When you want to improve the reliability you want to improve the resilience of the organisation, in the form of a specialized SRE team and/or in a collection of highly resilient teams, the culture (environment) and the safety are crucial, otherwise the Teams will not adapt their skills, and capabilities to the unknown unknowns [20].
Back to behavior management and learning
Most Security teams and companies improve the level of security by providing training. The training is often a combination of Telling (listing, reading) to help participant to transcend from “unconscious incompetent” via “conscious incompetent” to a level of “conscious competent” .See the figure below. By adding doing (action) to the training with for example coaching on the job or participating Pair testing, the trainees will become the desired “Conscious Competent” because they know what to do and can do it.
Motivate people to change their behaviour
The challenge is: how to influence the “Values and Believes” as positioned in the onion model, so that the level of security increases for the organisation as a whole by providing the newly learned “Skills and Capabilities” a sound foundation.
Since otherwise you have changed the “skills and capabilities” but the environment will never ask this “behavior” of the people you trained.
It appears there is a blind spot. Most current writing is on personal reflection but not on how to influence this from the outside or how to be trans-formative in your interaction. (see picture below)
Hack the system
The challenge is to find out how to influence the “Values and believes” of persons, this is the hacking of the Heart of people.
Hacking this for an individual person is difficult. The marketing and political industries are trying to perfection this, with for example trades as Neuro-marketing and behavioral economics.
Influencing separate individuals in an organisation is difficult to scale. Perhaps the iceberg model can be used if we treat it as a recursive model. I think the dark-blue-frame in the lower right can give us some help.
It can be reasoned that the models of the organisation (structures and mental models) that are shared between the employees provides a model for the shared “values and believe” and can provide a foundation for the behavior in the group.
Culture eats strategy for breakfast
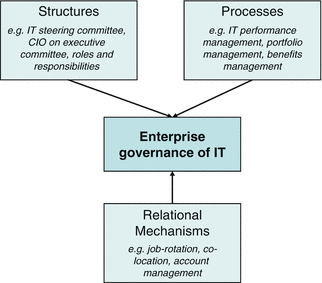
The “values and believe” of an organisation is also called the culture of an organisation. The inner working of an organisation is the result of the following [21], [22]:
- the organisational structures
- the processes
- the relational mechanisms
If I combine this with the part of the iceberg stating “structures and mental models”,then I believe that we can change the “values and believe” and “culture” of an organisation by doing the following two things:
- creating a clear shared mental model,
accompanied with - clear behavior as example by the leadership.
Conclusion
When we want to improve the level of security in an organisation, then we need to change the perception of security by “creating a clear shared mental model” and motivate the leadership into “clear example behavior”. This is the road to a sustainable improvement. I would even state that other approaches are less efficient and effective in increasing the security.
Next steps
For me personally I would like to look into the possible overlap between “the learning organisation” and the field of “Organisational behavior management”. Since the learning organisation states the importance of a shared vision and shared mental models, and is essential in the creation of a resilient organisation. Where OBM states that behavior of an organisation can be managed.Interesting topics, so much to do..
Tools
A powerful tool is making the iceberg explicit. Systems Innovation provides an empty iceberg canvas [23] including tools you can use in facilitating the creation of the explicit iceberg in a workshop. This is free to use (CC BY Attribution).
Systems Innovation also provides an example of applying the iceberg canvas [24].
Happy Hacking!
Edzo Botjes – Antifragility Architect – Xebia Security.
Reference
[1] 283226690Prodan, M., Prodan, A., & Purcarea, A. A. (2015). Three New Dimensions to People, Process, Technology Improvement Model. In A. Rocha, A. M. Correia, S. Costanzo, & L. P. Reis (Eds.), New Contributions in Information Systems and Technologies (Vol. 353, pp. 481–490). Springer International Publishing. /978-3-319-16486-1_47
[2] abstract/document/8065754Javaid, M. I., & Iqbal, M. M. W. (2017). A comprehensive people, process and technology(PPT) application model for Information Systems(IS) risk management in small/medium enterprises(SME).2017 International Conference on Communication Technologies(ComTech), 78–90. /COMTECH.2017.8065754
[3] Surviving Security: How to Integrate People, Process, and Technology Andress, A. (2001). Surviving Security: How to Integrate People, Process, and Technology, Second Edition.
[4] Human aspects of information security in organisations Safa, N. S., Solms, R. von, & Futcher, L. (2016). Human aspects of information security in organisations. Computer Fraud & Security, 2016(2), 15–18. Human aspects of information security in organisations
[5] principle based devops frameworks calmsDeBoer, E. (n.d.). CALMS: A Principle-based DevOps Framework. Retrieved February 15, 2021, from
principle based devops frameworks calms
[6] modern-agile-tools-for-successful-agile-transformationKaroliina Luoto. (2018, November 7). Modern agile – tools for successful agile transformation [Leadership & Management]. modern-agile-tools-for-successful-agile-transformation
[7] understanding-team-effectiveness/steps/identify-dynamics-of-effective-teams/re:Work – Guide: Understand team effectiveness. (n.d.). Retrieved February 15, 2021, from /understanding-team-effectiveness/steps/identify-dynamics-of-effective-teams/
[8] modern-agile-cause-agile-needed-a-refreshJohnny Ordóñez. (2016, October 18). Modern Agile -’Cause Agile needed a refresh![Presentations & Public Speaking]. modern-agile-cause-agile-needed-a-refresh
[9] Value-Based Enterprise Risk Management: Ergonomics, Ethics, and Organizational Structure Considered ApproachKucuk Yilmaz, A., & Flouris, T. G. (2019). Value-Based Enterprise Risk Management: Ergonomics, Ethics, and Organizational Structure Considered Approach. In A. Kucuk Yilmaz & T. G. Flouris (Eds.), Values, Ergonomics and Risk Management in Aviation Business Strategy (pp. 45–84). Springer. Value-Based Enterprise Risk Management: Ergonomics, Ethics, and Organizational Structure Considered Approach
[10] how-assess-your-organisation-cyber-security-resilienceHow to assess your organisation’s cyber security resilience. (n.d.). CIO. Retrieved February 15, 2021, from how-assess-your-organisation-cyber-security-resilience
[11] Foundations of Enterprise Governance and Enterprise EngineeringHoogervorst, J. A. P. (2018). Foundations of Enterprise Governance and Enterprise Engineering: Presenting the Employee-Centric Theory of Organization. Springer.
[12], M. S., & Archer, M. S. (1995). Realist Social Theory: The Morphogenetic Approach. Cambridge University Press. Realist Social Theory
[13] Against Structure: A Critique of Morphogenetic Social TheoryKing, A. (1999). Against Structure: A Critique of Morphogenetic Social Theory.The Sociological Review, 47(2), 199–227. https://doi.org/https://doi.org/10.1111/1467-954X.00170
[14] The processes of meaning making, starting from the morphogenetic theories of René ThomDe Luca Picione, R., & Francesca Freda, M. (2016). The processes of meaning making, starting from the morphogenetic theories of René Thom.Culture & Psychology, 22(1), 139–157.
[15] https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.53.9563&rep=rep1&type=pdfSa, J., Warboys, B., & Keane, J. (1993). OBM: A specification method for modelling organisational process.Proceedings of the Workshop on Constraint Processing at CSAM, 93.
[16] Waar-doen-we-het-voor.pdfKorthagen, F. A. J. (2001). Waar doen we het voor? Op zoek naar de essentie van goed leraarschap. IVLOS, Universiteit Utrecht, WCC.
[17] korthagen.nl/aandachtsgebieden/reflectie-en-kernreflectieReflectie en kernreflectie.(n.d.). Korthagen. Retrieved February 15, 2021, from korthagen.nl/aandachtsgebieden/reflectie-en-kernreflectie/
[18] researchgate.net/publication/312287103Sandu, A. & others. (2016). Using the pyramid of neurological levels in the human resources motivation management.Revista Românească Pentru Educaţie Multidimensională, 8(2), 31–44.
[19] lifemanagement.co.uk/index.php/2018/12/20/neurological-levelsTurner, J. (2018, December 20). Neurological Levels. JEFF TURNER Hypnotherapy & Life Management. lifemanagement.co.uk/index.php/2018/12/20/neurological-levels/
[20] doi.org/10.5281/zenodo.3719388Botjes, E. (2020). Defining Antifragility and the application on Organisation Design.doi.org/10.5281/zenodo.3719389
[21] isaca.nl/wp-content/uploads/Downloads/Risk%20Event/2018/Presentatie_Wim_Van_Grembergen_19-4-2018.pdfCOBIT 5 FOR, IT RISK MANAGEMENT, Prof. dr. Wim Van Grembergen, University of Antwerp (UA), IT Alignment and Governance (ITAG) Research Institute – Apr 2018 @ ISACA
[22] link.springer.com/chapter/10.1007/978-3-319-14547-1_2De Haes, S., & Van Grembergen, W. (2015). Enterprise Governance of IT. In S. De Haes & W. Van Grembergen (Eds.), Enterprise Governance of Information Technology: Achieving Alignment and Value, Featuring COBIT 5 (pp. 11–43). Springer International Publishing. doi.org/10.1007/978-3-319-14547-1_2
[23] systemsinnovation.io/post/iceberg-canvasInnovation, S. (2020, December 14).Iceberg Canvas. Systems Innovation. systemsinnovation.io/post/iceberg-canvas
[24] systemsinnovation.io/post/leverage-points-canvasInnovation, S. (2021, January 22).Leverage Points Canvas. Systems Innovation. systemsinnovation.io/post/leverage-points-canvas
—-
Xebia’s core values are: People First, Sharing Knowledge, Quality without Compromise and Customer Intimacy. That is why this blog entry is published under the License of Creative Commons Attribution-ShareAlike 4.0