As the world remembers 2020 for COVID pandemic, in the cyber world 2014 will long be remembered for a series of mega security breaches and attacks. Well known mega breaches in 2014 in the order of magnitude are:
- Target (40 million Credit and debit card details stolen)
- eBay (145 million people affected)
- JPMorgan Chase & Co. (76 million households and 7 million small businesses affected)
- Home Depot (56 million unique payment cards)
- CHS community Health Systems (4.5 million people affected)
- Michaels Stores (2.6 million people affected)
- Nieman Marcus (1.1 million people affected)
- Staples (point-of-sales systems at 115 of its more than 1,400 retail stores)
- Sony (Employees personal data and corporate correspondence)
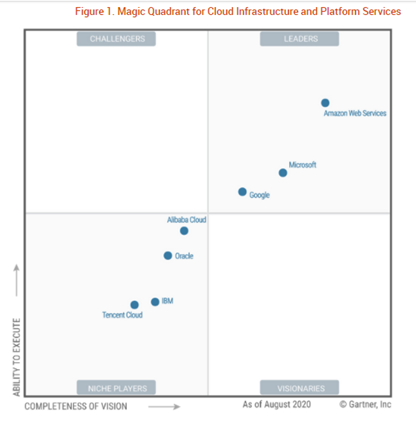
Cloud computing in 2020 is more mature, going multi-cloud, and likely to become more focused on vertical and a sales ground war as the leading vendors battle for the market share.
Picking the top cloud services provider is not easy given that the answer, much like enterprise software and IT in general boils down to "Hmm, it depends."
A few key trends are emerging for cloud computing in 2020, at a high level:
- Move to remote work. Video conferencing and collaboration tools are accelerating moves to the cloud.
- Companies are well aware of vendor lock-in and want to abstract their applications, so they can fly across clouds.
- The game is all about data acquisition. The more corporate data that resides in a cloud the stickier the customer is to the vendor.
- AI, Analytics, IoT, and edge computing will be differentiators among the top cloud service providers, as well serverless and managed services.
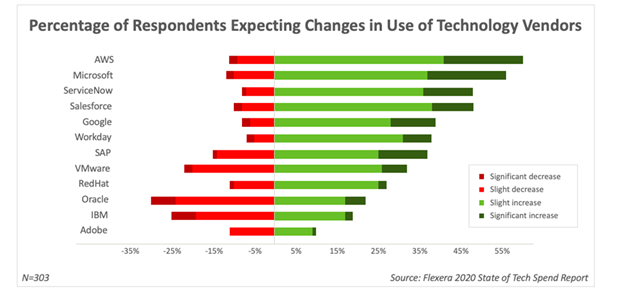
- Public cloud spending has hit an inflection point where it has passed traditional IT infrastructure (In the second quarter of 2020). Spending including public and private cloud environments has increased 34.4% from a year ago. Non-cloud IT spending fell 8%.
- Software as a service(SaaS) is expected to be the largest revenue slice of the cloud pie. According to Gartner, SaaS revenue in 2020 is expected to be 166 billion USD compared to 61.3 billion USD for IaaS.
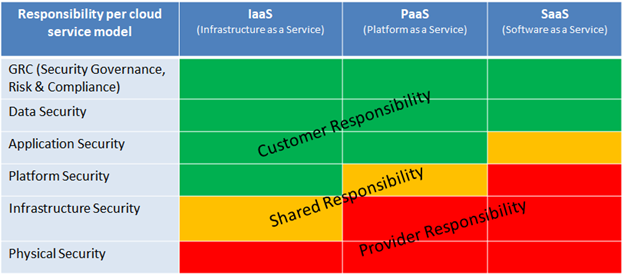
However, the major hurdle in adopting Cloud is the security risks associated with it. While the fear is reasonable, it is also important to understand that security risks can be mitigated and dealt with efficiently, as long as the organization is aware and prepared for any security and data breaches.
Most companies fail to understand cloud security. In fact the security of your cloud infra lies mostly on the shoulders of your company and not the CSP -cloud service provider.
The shared responsibility model is similar across the service provider landscape. To break it down simply there are 2 distinct cloud security roles and responsibilities:
- Security “OF” the cloud (Cloud Service Providers)
- Security “IN” the cloud (Your Company)
Here are the top 10 steps to share your responsibility towards achieving and maintaining enterprise cloud security:
1. Encrypt your cloud data
In the cloud, your enterprise is still working with the data. Any type of data you store in the cloud is to be encrypted in order to prevent harmful actors from intercepting it. Encryption techniques can help protect data. Encryption has also negatively impact system performance, balancing is crucial what to encrypt and what not to.
2. Misconfiguration
Misconfig occurs when computing assets are set up incorrectly. Few common examples include: Unsecured data storage or containers, Excessive permissions, Default credentials and settings left unchanged.
Cloud based resources are highly complex and dynamic, poses a challenge to configure. Traditional controls and change management approaches are not effective in the cloud. Companies should embrace the automation and employ technologies that can scan continuously for misconfigured resources and remediate problems in real-time.
3. Have data backup and recovery plans
Security threat actors might destroy your data or otherwise make it unusable (through data corruption, for example). Your business needs data backup and recovery plans to help mitigate any potential destructive breaches. You can either use managed services or design cloud architecture in a way to handle regular backups in desired locations.
4. Monitor your cloud environment
Enterprises can’t just operate blindly in the cloud. They need to understand how their cloud deployment is working at all times. There is a need to monitor your cloud environment to examine factors such as performance, speed, and security. For security monitoring, be vigilant and pay close attention to user activities and the access logs.
5. Improve security from the user’s end
The first step in achieving and maintaining the cloud security for users is to train your workers on the cloud environment that your business is using. Improper usage of the cloud won’t just lead to inefficiency; it also opens the doors to your workers accidentally causing a security breach.
6. Security
Cloud computing introduces several changes to the conventional internal system management practices related to IAM (identity and access management). Secure accounts with 2-factor authentication and limit the use of root accounts. Practice the strict identity and access controls for cloud users. Rotate keys, remove unused credentials or access privileges and employ central, programmatic key management. Segregate and segment accounts, VPCs and identity groups based on business needs (and the principle of least privilege).
7. Interfaces and APIs
Practice better API hygiene. Best practice includes diligent oversight of items such as inventory, testing, auditing and abnormal activity protections. Avoid re-user and ensure proper protection of API keys. Consider using standard and open API frameworks for ex: Open Cloud Computing Interface (OCCI) and Cloud Infrastructure Management Interface (CIMI).
8. Understand the security requirements of the exit process
It’s crucial that once the customer is done with the termination process, ‘reversibility’ is achieved. Meaning, customer’s data should not remain with the cloud service provider. The provider must ensure that any copies of the data are permanently erased from their environment, wherever the copies may have been stored, including backup locations and online data stores.
9. Stop unauthorized devices from accessing business cloud services
Most organizations operate business cloud services from multiple vendors. If an unauthorized device gets access to any of the services, the data becomes vulnerable and can go out of control. This happens when an end user downloads a company app to a personal device for the convenience. Unless IT can delete apps and control data sharing on that device, business data should never be on any device.
IT must be able to implement these security controls throughout its business cloud services, irrespective of the supplier so that it can prevent unauthorized devices access to business data.
10. Provide rich security controls for all operating systems
It’s not just a Windows world anymore. These days, most companies support a range of operating systems. Older operating systems such as Windows 7 have legacy security tools, while modern operating systems such as Windows 10, Android, iOS, Linux and macOS, have evolved to provide unified, cross-platform security solutions.
IT should select a solution that offers rich controls that take full advantage of the native safety frameworks of the different operating systems.







