Deploying Google Cloud (GCP) resources via Azure Pipelines used to require service account keys. Today, however, Azure DevOps OIDC tokens can be exchanged to Google credentials using Google Cloud Workload Identity Federation. This blog uses the Google Cloud Auth to do so.
Azure DevOps Google Cloud Deployment Pipeline Overview
The high-level deployment pipeline consists of two steps. First, the Google Credentials are exchanged. Second, the Google Cloud deployment is executed.
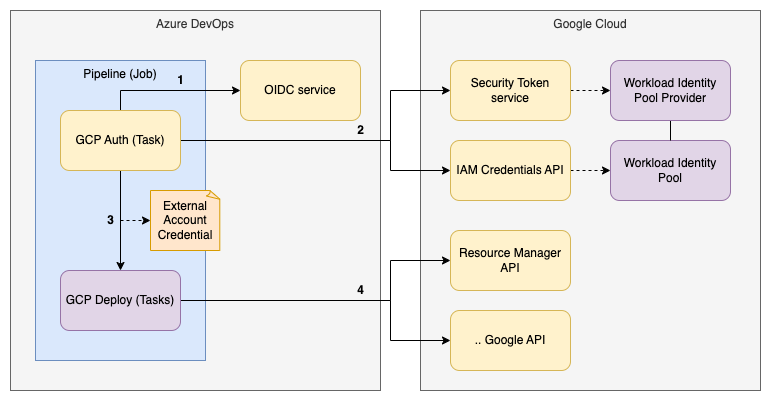
Use this blog to configure Google Cloud Workload Identity Federation for Azure DevOps.
Azure Pipeline Configuration
An example Terraform deployment pipeline is configured below:
steps:
- task: GcpWifAuth@0
inputs:
connectedServiceId: gcp-wip-ado
- task: TerraformInstaller@1
inputs:
terraformVersion: 'latest'
- task: Bash@3
inputs:
targetType: 'inline'
script: 'terraform init'
workingDirectory: 'terraform'
- task: Bash@3
inputs:
targetType: 'inline'
script: 'terraform apply -auto-approve'
workingDirectory: 'terraform'
The GcpWifAuth-task initializes an external account credentials-file and points the GOOGLE_APPLICATION_CREDENTIALS to it. The Google Auth library, as a result, will exchange the Azure DevOps OIDC token for a Google credential.
The credentials are executable-sourced, because the Create OIDC token url requires a POST method. Consequently, the
GOOGLE_EXTERNAL_ACCOUNT_ALLOW_EXECUTABLESis exported as well.
Google Cloud Workload Identity Federation Service Connection
The GcpWifAuth-task requires a service connection to authorize the pipeline for a specific Google Cloud resource. This Google Cloud Workload Identity Federation service connection specifies the workload identity pool provider and optionally the service account to assume:
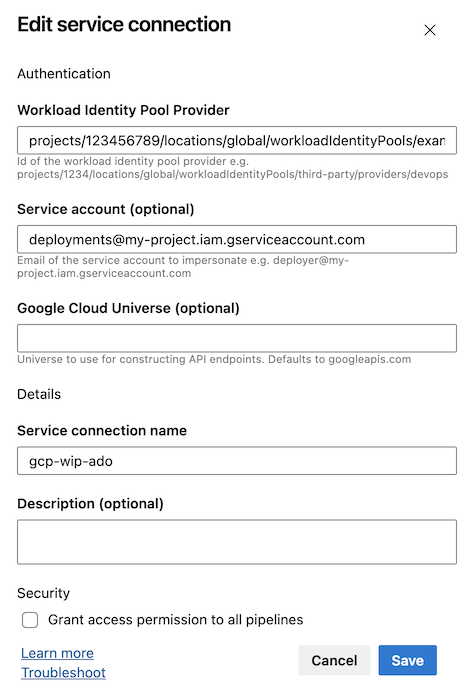
Bonus: Overriding The Assumed Service Account
The assumed service account, optionally, can be overriden in the step definition. This enables you to manage a single Workload Identity Pool Provider and Service connection, while accessing multiple service accounts. Note, however, that the Azure DevOps token only indicates that the pipeline is granted access to the Service connection, and not the target service account.
steps:
- task: GcpWifAuth@0
inputs:
connectedServiceId: gcp-wip-ado
serviceAccount: special-deployment@my-project.iam.gserviceaccount.com
Conclusion
Replace service account keys with federated Google credentials. Reduce credential management using the GcpWifAuth-task.
Image by RENE RAUSCHENBERGER from Pixabay




